Fundamentals#
This chapter starts with basics and covers a few bits of info and best practices that everyone who uses computers regularly will benefit from knowing. We’ll build more superpowers based on this foundation in the later chapters.
Basic parts of computers#
Computers bring in, manipulate, and present data with lightning speed and hardly any moving parts. This is why they’ve had such a massive impact on our lives, and have brought forth the information age. For a bit of context, here are the key components in computers that perform all that wonder:
Component |
Purpose |
|---|---|
Central Processor Unit |
The CPU is the brain and does most of the number crunching. Faster is better, speed is measured in billions of computation cycles per second (gigahertz). |
Memory (RAM) |
The working short-term fast-acting memory; it holds the data while the CPU crunches it. More is better, measured in billions of octets of ones and zeros (gigabytes). |
Hard drive |
The long-term but slower memory. It saves your files and photos and spreadsheets. Also measured in gigabytes. |
Monitor |
Displays information visually. On phones, it’s an input device too. Measured in the number of horizontal and vertical picture elements (pixels). |
Network card |
Sends and receives data to/from other computers for posting cat pictures, etc. Measured in billions of ones and zeros communicated per second (Gbps). |
Operating systems#
When a computer turns on, a series of simple built-in operations run to check the processor and memory, and to figure out what other hardware is attached. Eventually, enough systems are online to read larger and more complex programs from the hard disk. In a sense, the computer is pulling itself up by its bootstraps (hence the term “booting up”). At this point, the computer will find an Operating System (OS) on the hard disk, which will tell the computer how to run everyday programs like an office suite or a web browser and everything else.
There are many OSs out there, but we’re going to mostly just talk about three of them: Microsoft Windows, Apple macOS, and Linux. The first two are familiar to everyone. The third is an open-source product (meaning it’s available for anyone for free and that anyone can look at its underlying source code) developed over the years by a community of volunteers and professionals. Linux is the underlying technology behind Google’s Android OS and also runs many of the servers powering the internet. In the past few years, more people started running Linux on their personal laptops and desktops as a powerful, cost-effective, fun, and philosophically-pure alternative. We’ll try hard to make sure everything discussed in this book works fine in all three of these OSs.
Files and folders#
As you probably know, most computer systems store information in a hierarchical structure of nested digital folders (aka directories) on the hard drive. You put your photos in the Photos folder, and so on. You can create folders and files, delete them, rename them, copy them, paste them, etc.
Note
If you are unfamiliar with copy/paste, you are in for a treat. It is a core
superpower but you may benefit more from this book after learning about it. The WikiHow
page on it is fantastic. I’d also be a little worried that this book is slightly too
advanced for you. If you already know about copy/paste but not the keyboard shortcuts
(Ctrl-C, Ctrl-V) just know that those shortcuts are speed-demons.
We’ve all lost files in folders before. Many of us have opened a document from e-mail and worked on it all day only to close the editor and then never find the file again. This usually happens when it gets saved to some temporary folder where files downloaded from the internet go. I’ve done this myself many times, and have fielded dozens of calls for help from friends through the years due to this. The solution is the Save As button, which is distinct from Save in that it lets you choose where to save a file as opposed to just saving it where it was opened from. Click it, navigate to a normal place like Documents, and save it there. Problem solved!
Organizing folders is an ongoing battle for many of us as well. We try breaking things down by
file type (Photos, Documents, Music) and then by year. Sometimes for multi-year projects,
it doesn’t go well and you may need a Projects folder. It’s deeply personal, so just
explore what works best for you. For photos, one nice method is to
organize them by year and then name subfolders with the month and then an incrementing
integer and an event, like 07.1 Fourth of July or 12.4 Yodit's Christmas Sweater
Party. Operating system designers are often trying
to move away from the hierarchical structure and use tags (so a file can have multiple
tags, similar to being in multiple folders at once) but we’re not quite there yet.
Backups#
Backups are really important, and I don’t know a lot of people who take them very seriously besides professional IT staff. I personally am really obsessed with my document, photo, and music collections and would be just heartbroken if I lost them in a fire, robbery, hardware failure, electromagnetic pulse, earthquake, volcano, and/or nuclear war. But even I am not great with backups. The main categories of data loss to protect against are:
Hardware fails and data can’t be recovered
Hardware is stolen or hacked and can’t be recovered
User (or family member) accidentally deletes data
A reasonable and easy solution for backups is the cloud which we will discuss momentarily.
A more-difficult-to-implement but conceptually straightforward method for slow-moving data is to buy two external USB hard drives with a few terabytes of space. Copy all your important files over to them both. Take one to work or a friend’s house or some other off-site location. Every month or six months or whenever (depends on your pace of accumulating new stuff that you care about), copy new files onto them and swap them. This will protect your archival data against robbery and fire but not necessarily earthquakes or EMPs. For those, you need more distance.
Of course, there’s the challenge of finding out which files are out of date, and having the discipline to regularly update the backups. Figuring this out and quickly synchronizing is the job of the thousands of backup software products you’ll hear about out on the market. Sure, you could just copy everything over every day, but that would take a long time and wear out your disks. Most modern operating systems like Windows, Linux, and macOS come with backup utilities. Try those out or look for third-party commercial products.
As your digital superpowers develop, you will become knowledgeable in a few other systems
that will lead you to exceedingly slick backup options. git-annex is an advanced
option worth noting that builds on the git tool you’ll learn about in
Programming. It’s quite powerful for keeping well-organized and
secure backups. For scientific, engineering, and data users, the datalad tool builds
further upon git-annex to add reproducibility on top of backups, so your scientific
results can be perfectly replicated by anyone in the future. In particular, datalad
auto-discovers any output files created by running particular commands and tracks the
input, commands, and output.
Network Attached Storage (NAS)#
It’s not too uncommon these days to have a NAS in the home. These are lightweight computer/appliances containing big hard drives that you can connect to your home computers. Professional photographers and videographers all have these. They offer some benefits in terms of sharing files across the family’s computers and in terms of data reliability (they’re often resilient against a single failure of one hard drive). You can buy them for a few hundred bucks or, if you’re into the hobby of it, you can turn an old computer into a NAS. PC Magazine (bless their hearts) runs a review of the latest and greatest NAS machines every year, so check them out for more advice.
Warning
NAS provides some level of backup, but they do not help in the event of fires, burglary, or sometimes even accidental deletion. Some NAS products come with nicely polished backup software that can help with your offsite backups.
File Encryption#
If your phone or laptop gets lost or stolen with all your work and online dating on it, no problem, right? Because you have a backup? Great job! But you may still worry because there’s a lot of personal and confidential stuff on most devices. It’s wise to keep your private matters private no matter if they’re just your mom’s recipes. You DO have something to hide! If someone gets access to your e-mail for instance, they can reset your bank password and cause all sorts of ruckus. So let’s just hide your data.
Encryption is the process of scrambling the bits on your hard drive in such a fashion that even if someone steals the computer/phone, they will not be able to access the information within. Without encryption, a bad guy or random teen could just plug a cable in and see all your information. Math to the rescue!
Options for encrypting your hard drives in different systems:
Kind of computer |
Encryption options |
|---|---|
Windows |
Find the BitLocker program and activate full-disk encryption |
Linux PC |
Choose to encrypt entire drive during installation. |
Mac |
Find the FileVault utility and set it to encrypt the full disk |
Android phone |
Search settings for “Encryption” and ensure it is enabled. If not, enable it. Make sure to set a strong PIN or other credential |
iPhone |
Almost always encrypted by default; set a strong PIN |
Warning
If you encrypt something and then forget the password, your data is very nearly impossible to recover (by design, after all that is the point). Hopefully you have a backup! This seems obvious but it is a little scary. Just be careful.
The Cloud#
The Cloud is a nebulous term that really just means “a large semi-automated collection of nearly identical computers out there on the internet that is operated by some company.” A lot of computation is moving to The Cloud because of the efficiencies of scale inherent to mega-operators like Amazon Web Services. The deal The Cloud offers to new business owners is that they will deal with the hassle of procuring, maintaining, and servicing the computers, allowing you to focus on software, marketing, and users. In other words, you do you. If you do really well and need 10,000 new computers right now, they click a button and (bloop-bleep) it’s done. If you mess up and everyone starts deleting their account on your service, (bleep-bloop) those computers are no longer reserved for you. What a deal! Services like Netflix and Uber run on cloud-based back ends operated by other companies, like Amazon, Google, or Microsoft.
What does it mean to you? Many services offer the ability to automatically synchronize files on your hard drive with their hard drives in the cloud (via the network card). This is nice because when you take a photo on your phone, it shows up on your computer. If you experience a tsunami, anything that was synced in The Cloud far away will survive and re-sync when you get a new computer.
Services like Dropbox, Microsoft’s OneDrive, and Apple’s iCloud do this. If you’re uninterested in running your own server or dealing with your own backups, I have to recommend using these services. The risk, as always, is that you have to trust them, because they can see all of your files. Also, with computer systems being so complex, they always have some new severe vulnerability, so it’s probably just a matter of time until these services are breached. At that point, the biggest services will be the most likely target. On the other hand, they also probably have the best defenses. Just something to think about.
It’s the same story with e-mail. If you use a web-based e-mail system in the cloud you can just log on from anyone’s computer and have it.
The command line#
Vast computer superpowers are controlled by a somewhat-obscure window into your computer:
The Command Line (or Terminal). Go onto your computer and launch it. On Windows, click
Start, and type cmd and click Command Line when you see it (or just press
enter). On macOS, go to the Finder and then click Go → Utilities → Terminal.
In Linux, just hit Ctrl-Alt-T. A little box will pop up with an ominous blinking
prompt. That’s it. That’s the command line. You’re gaping into a universe of
possibility, like in Men in Black when they gape into the cat’s necklace and it’s a
whole galaxy.
The idea here is that you type commands in and it responds by doing something. These commands are precise, expressive, and repeatable; you can tell the computer exactly what you want and it will do it. As you’ll see in later chapters, this can be significantly faster than pointing and clicking, especially for repeated actions. In other words, a command is worth a thousand clicks.
Most importantly, hundreds of grand-slam superpowers are hidden in small and simple command-line utilities, the majority of which are freely available. The elegant design benefit that led to the existence of these rich tools is one of reductionism: many complex operations can be broken down into a series of simple operations. For example, consider a spell-checker from a software developer’s perspective. If she writes a word processor and needs spell checking, she can either write an entire spell-checker in addition to the word processor, OR pray that someone else has made a spell-checker before and made it available for her to pull in and use. As it turns out there is indeed a spell-checker library and utility that’s available in this regard and it has a command-line interface. Thousands of such building blocks exist, and they’re all available to you right now through the command line.
There is a reputation that the command line is for “advanced” users only. I don’t think this is true at all, and I hope I can convince you that it’s accessible and useful for everyone. We’ll leverage the command line quite frequently in this book.
Note
When you read something like “Type this in” from now, and it’s unclear where to type it, it’s very likely the command line.
Let’s type some commands in to see that it’s fun and easy.
Operation |
Windows |
Linux/macOS |
|---|---|---|
Which folder am I in? |
|
|
What files exist in this folder? |
|
|
Move up one folder in the hierarchy |
|
|
Move back to the original folder, |
|
|
Print the current time and date |
|
|
Print the computer’s uptime |
|
|
Make a folder |
|
|
Remove a folder |
|
|
Convert units |
|
|
Make a cow say something |
N/A :( |
|
That last one is not a joke.
Some commands come with an OS and others have to be installed from a third party. The last
two examples above are the latter, and the installation of units is discussed
in Unit conversion, so you’ll actually have to wait until then to try out that command.
Here are a few productivity enhancers in the command line:
If you ever want to get the previous command again (to either rerun it or modify it slightly and then rerun it), press the up arrow on your keyboard. Each time you press it goes up in a history of all the commands you’ve executed. The down arrow goes in the other direction.
If you’re typing out a command you can often press
TABto auto-complete it. For instance, if there is a folder calledmy_very_long_folder_nameyou can just typecd my_veryand then pressTABand it will fill in the rest. This is called tab completion. I cringe badly and then speak up when people don’t use it because it can save hours per day when you’re working heavily in the command line.You can copy and paste commands into the command line.
At least in Windows, you can drag a file into the command line instead of typing its full path.
If you ever typed a command that’s taking too long or isn’t what you wanted, you can abort it by pressing and holding the CTRL key and then pressing C.
Programs and package managers#
Your computer undoubtedly came with some programs, and you have probably downloaded and installed others. It was once a big pain to go out and find/install the latest versions of various programs and to keep them up to date. In the Linux world, this was solved years ago with special programs called Package managers, which are simple little commands that know how to go find, download, install, keep up-to-date, and (if desired) uninstall programs. macOS and Windows have started catching up and there are now good package managers for them as well. Without further ado, it’s time for your next superpower: package management!
Note
This is optional but will make it easier to follow along in sections of the book that rely on special programs. In all future uses, you can alternatively search for the program at hand, find its web page, download it, and run its installer.
Warning
These programs change what’s on your computer (that’s the point). It is unlikely but possible that something will go wrong. Try these out on a computer that you can afford to break if you’re just learning.
macOS has one de-facto standard package manager called Homebrew that can be installed from the command line by running the following command (which is also on their webpage if you’d like to copy/paste it):
/usr/bin/ruby -e "$(curl -fsSL https://raw.githubusercontent.com/Homebrew/install/master/install)"
A good package manager called Chocolatey is available on Windows. To get it, you have to
open the Command Prompt with Administrative privileges, meaning commands you type can
change system settings. You generally do this by typing cmd in the Start Menu and
clicking the choice that has the word “Administrator” in it (or by right-clicking the
normal Command Prompt choice and choosing “Run as Administrator”). Once you’re in,
copy/paste the command shown at https://chocolatey.org/install into it and press
Enter to run it (it’s simply too long to reasonably put in this book expecting you
to type it). You may have to right-click and choose Paste to paste, or (in Windows)
just press Control-V.
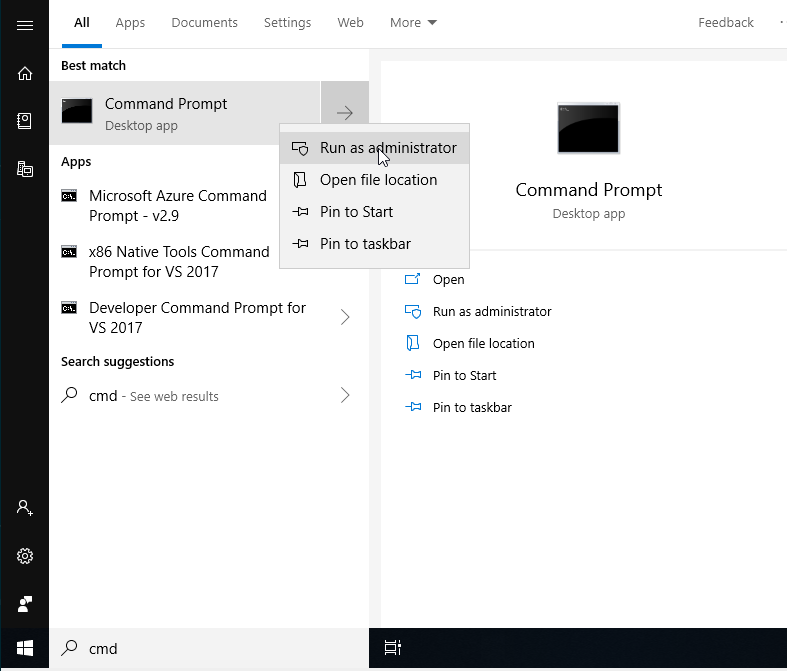
Opening the Administrator Command Line in Windows 10 (hover your mouse over and
right-click, then left click on the Administrator option). You generally have to use
the Administrator option every time you run a choco command.#
Now you have a package manager and can install common programs with simple commands! The commands will look similar to what’s shown below. We’ll provide similar tables frequently.
OS |
Command |
|---|---|
Windows |
|
Linux |
|
macOS |
|
After issuing a command like these, there may be some prompts and alerts that scroll by as
the packages are downloaded and installed. In some cases, if things look frozen, you may
have to just press Enter (I had to do this in choco a few times). If you install a
large package, the process may take a few minutes depending on your internet connection
speed.
Note
In Windows with choco you have to either run refreshenv or open a new
command terminal after you install a program before it is available as a new command-line
program.
You can just as easily uninstall anything installed through these systems by running the
same kind of command but with uninstall or remove instead of install. And you
can update as well.
Life’s getting easier already! Let’s put that new skill to work.
Password managers#
You know that feeling when you are trying to buy something and the web page forces you to make a new account? Many of us just reuse the same old password again and again, maybe with a few modifications based on the site name. This ends up being really dangerous in addition to annoying because the likelihood that Arnold’s Pizza Shop has rock-solid security practices is low, and after you give (roughly) the same password to a billion such establishments, the probability of some nefarious hacker breaking into them and getting your password approaches 100%.
Annoying and dangerous!? Hopefully there’s a superpower for that. Indeed, there is: Password Managers. Password managers are programs you run on your computer or phone that do two essential things:
They act as your own personal encrypted vault of passwords so you can look them up easily when you need them
They have random password generators that will whip up a 25-character password whenever you need a new one for Arnold’s Pizza Shop or similar
If you use a unique and random password for everything, the threat discussed above is neutralized. Plus you don’t have to type in the password ever, Password Managers allow you to copy it and then paste it right into the web form. In this workflow, you never actually know most of your passwords.
Tip
You will still need to memorize a few key passwords for extra-important accounts. Just keep them unique. See Making secure but memorizable passwords with Diceware below for ways to do this well.
There are some great open-source password managers out there like KeePassXC as well as commercial offerings (with better support) such as LastPass or 1Password. A good combo is to put your KeePassXC database in a cloud synchronization program so it synchronizes across all your devices.
To try out KeePassXC with a package manager (see above), run the following in the Command Line:
OS |
Command |
|---|---|
Windows |
|
Linux |
|
macOS |
|
You may also want to store credit cards in your password manager, making it really easy to copy/paste them into web forms when shopping.
Of course there is a new threat now: If someone finds out the one password you use for your password manager and has access to your files, they can get all of your passwords at once. This is less likely to happen, but you should consider it when typing your master password into the password manager. Keep in mind that Edward Snowden puts a blanket over his head whenever he types a password, and he’s somebody who knows what’s going on out there.
Tip
Does your password at work auto-expire every few months? Companies used to think this was good for security but in 2016, NIST released guidelines saying that unnecessary auto-expiry was leading people to choose weak passwords. They now recommend to only force someone to change a password if there’s been evidence of a data breach. Same with password complexity (it’s no longer wise to require mixes of uppercase and symbols), just make a long password and check it against a common password list.
Making secure but memorizable passwords with Diceware#
For the few very strong passwords you do need to memorize, the Diceware method is here to help. Here are the steps:
Grab a Diceware word list like one of these from the EFF. These have 5-digits between 1 and 6 (for each possible value of a die). Here is an excerpt:
46663 reflex 46664 reflux 46665 refocus 46666 refold 51111 reforest 51112 reformat 51113 reformed 51114 reformer
Get 5 dice and roll them. Line them up and then look up the word that corresponds to the values you rolled (if you had 4, 6, 6, 6, 4, your first word would be
reflux, from the list above).Roll 4–7 more times. Now you have 5–8 random words. String them together and that’s your super-secure but still memorizable password.
Note
Don’t have 5 dice sitting around? You can find online generators of diceware passwords. Just know that they aren’t random enough and the Diceware method recommends against using anything but actual dice. Besides, everyone should have some dice around for playing 10,000 [1].
Two-factor authentication#
Two-factor authentication (2FA) is a login method offered by many web pages and institutions these days. It makes it so you have to type a password and also type in a one-time code sent to your phone via text or through a special app. The idea here is to combine something you know (your password) with something you have (your phone). It’s similar to typing your zip code at the gas pump when using a credit card [2], or a PIN with a ATM card. For your most important accounts, it’s really essential to turn it on to minimize the likelihood that someone can access them. Banks, big shopping sites, and e-mail providers are good first places to start. You can learn how to activate it with a web search along the lines of:
activate [web page name] two-factor authentication
The new risks here are that it takes longer to log in and, if you lose your phone, it’s extra hard to just reset your password. Such are the tradeoffs. Many companies are relaxing the pain by only requiring that you use the 2FA code on new computers so it’s not all that bad. Other companies make you obtain and enter a 2FA token twice per transaction, which is really annoying.
Warning
Getting 2FA tokens through text messages is probably better than nothing, but it’s significantly less safe than using a dedicated 2FA app. Why? Because it’s possible for a bad guy to use social engineering to convince your phone operator to change your phone number to a different SIM card, thereby allowing them to access your 2FA tokens and get into your accounts. This has happened in serious attacks, such as one on CloudFlare in 2012. It’s much harder for them to get access to an app on your phone.
Common scams#
Billions of dollars are lost each year to fraud, much of which occurs on computers. You should always be a little skeptical if someone you don’t know asks you to pay for anything or give you access. Here are a few guidelines for avoiding fraud.
Never give your password out
No well-meaning entity will ever ask you for your password on the phone or in e-mail or in any other place than a log-in form. If this ever happens to you, you should recognize it as a huge red flag.
Computer companies will never call you
There are lots of scams where people pretend to be calling from some big company you’ve heard of offering to fix something on your computer if you just go to a certain link. This is someone trying to access your PC to find banking information about you. Hang up!
E-mails where people know an old password of yours don’t have video of you
Through the years, various companies have experienced data breaches. If you had an account with any of them with a weak password (i.e. a single dictionary word), they may e-mail you and say they know your password and claim that they hacked into your computer and recorded you doing something naked or private. They threaten they’ll send it to all your friends if you don’t send them about $1000 via Bitcoin. It’s very unlikely they have anything on you since these breaches are widely available. If you used that same password on other accounts, you do need to change it, like, yesterday. See https://haveibeenpwned.com/ for help in checking to see which accounts of yours have been compromised in known breaches.
If someone tells you that you’re in big trouble, but they can help, it’s probably a scam
You may get a call saying that you have dozens of unpaid violations at [your county courthouse] but if you go down to Walgreens and get $2000 worth of gift cards and read them one after the other to this person on the phone they’ll get you out of it. That’s a scam. Gift cards are very hard to trace and are a favorite instrument of scammers. If you’re in actual trouble just deal with it through the proper channels and get a lawyer. This happens with people impersonating the IRS as well. They may know a little about you, like where you live and some previous addresses. This is all public record but it makes the scam seem more real. Don’t fall for it. If you’re really unsure, ask them for the number of their institution, check it online, and then call them back.
Watch out for phishing
Phishers will send you an e-mail that looks like it’s from a familiar institution. It will have the right logos, the right address, and will have a link you can click to do something important, like reset a password or confirm something. The best defense here is to hover your mouse over the link and take a look in the address bar (usually at the bottom of the screen) to see where the link is actually going. If it’s to some weird internet address or some misspelling of the actual site, it’s a scam. If you do click the link, you can also check the address bar of the web browser. Be careful, these can be very tricky. This has been such a problem that your employer may hire someone to send phishing-like messages to you and if you click them you’ll have to take mandatory training. It’s like anti-phishing phishing.
Ransomware is real
If you get a message that all your files are encrypted and you have to pay to get them decrypted, it may be real; especially if you can’t access your files. Ideally, you’ll have a backup of your files and can just wipe your computer clean and restore the backup. Otherwise, you have to choose whether you want to give the criminal what they want or kiss your files goodbye. Another good reason to have backups!
Those are just a few. The FBI has hundreds more to watch out for at https://www.fbi.gov/scams-and-safety/common-fraud-schemes.
Well, that sums up chapter one. I hope you’ve learned something new and useful.
Footnotes