Around the House#
You browse the web through your phone and computers at home, you print stuff, you e-mail friends, you learn, you play. In this chapter, we’ll make these more pleasant, productive, and safe.
Life-changing keyboard shortcuts#
You probably use a keyboard, at least a little. A few subtly-sublime keyboard shortcuts can really speed up your work and play. You may have heard that professional typists never click around in a word to go back and make corrections, they just delete the world and hammer it out again in under a second. These shortcuts can help you when changing text in anything (e-mail, word processor, web browser, etc.). Anything you can do to prevent yourself from switching from keyboard to mouse and back is going to turbocharge you. If you think about it, the keyboard is more expressive than a mouse. Try them out; you’ll love them!
Effect |
Windows/Linux |
macOS |
|---|---|---|
Delete previous entire word |
Control-Backspace |
Option-Delete |
Delete next entire word |
Control-Delete |
Function-Delete |
Move cursor to previous or next word |
Control-LEFT, Control-RIGHT |
Option-LEFT, Option-RIGHT |
Move cursor to beginning of line |
Home |
Control-A |
Move cursor to end of line |
End |
Control-E |
Move cursor to beginning of document |
Control-Home |
Command-Up |
Move cursor to end of document |
Control-End |
Command-Down |
Here’s the kicker: for all of these “move cursor” shortcuts, you can throw a SHIFT in there as well to select everything from where you are now to where the cursor’s going to go. Once something is selected you can delete it, copy it, change the formatting… You can do anything!
Exercise
Try these out. Open an e-mail editor and type out a sentence of your choosing. Now don’t leave the keyboard! From the end of the sentence press Shift-Control-Left (to select the previous word) and then press Left three more times (while keeping Shift-Control held). This should have selected the previous three words. Copy them with Control-C, press End, and press Control-V a few times to paste them.
Now try Control-Shift-Home followed by Backspace. You’re really hauling now!
(macOS people use the equivalents from the table above)
I didn’t learn Control-backspace until well into my career and it has really been useful since then.
Besides editing text, keyboard shortcuts can streamline web-browsing too. The same “leaving the keyboard is slow” philosophy applies online in its own way. The most essential shortcut takes you to the address bar with Control-L (Command-L on a Mac). Now you can type a new web address or a search and just press enter to proceed.
To turbocharge this, combine it with the !bangs feature of the DuckDuckGo search
engine and you’ll really be moving. If you set DuckDuckGo as your default search provider
(something you can do in the settings of your web browser), then you can put, for
instance, a !t anywhere in the search and it will take you directly to the thesaurus
page for your search term. So big !t goes to a thesaurus page for the word big.
Thousands of bang codes are available, and you can even submit your own. Here are
a few more good ones:
|
|
|
|
|
|
|
|
|
|
|
|
That’s right, if you whimsically want to conjure up your ex-boyfriend while you’re in the
middle of reading a news article, you can just type Control-L !fb Jacob
Olson Enter and there he will be. Sigh.
Dozens of other keyboard shortcuts are available in various browsers. See if you can find the list of them (usually in Help → Keyboard shortcuts) and see if any others seem useful to you.
Avoiding printer dry-out#
Printers have a bad reputation for never working right and having really expensive ink. Regarding the ink issue, InkJet printer jets dry out if they’re not used frequently. So if you’re shocked by a printer never really working or always needing its jets cleaned, that’s why. If you print less than once a month but still really need that printer when you need it, consider getting a laser printer instead. They’re a bit more expensive (especially for color or combo printer/scanner), and their color for photo-printing is not as good, but their ink reliability is usually worth it for a lot of people.
Get to know your router#
Home networks consist of public internet coming in from your internet service provider
(e.g. Comcast) and going into your router which distributes it around your house via
Wi-Fi radio waves and sometimes Ethernet cables. Your router and each device connected to
it gets assigned Internet Protocol (IP) addresses, which are like street addresses, but for
the internet backbone. There exist a few special blocks of IP addresses for local networks
(e.g. the one in your home), and the most common of these is anything that starts with
192.168.
![digraph fig {
isp [label=<Public internet via ISP<br /><FONT FACE="Courier">82.234.111.239</FONT>>];
neighbor [label=<Your neighbor<br /><FONT FACE="Courier">82.234.111.240</FONT>>];
neighbor_wifi [label=<Neighbor's router<br /><FONT FACE="Courier">192.168.1.1</FONT>>];
router [label=<Your Router<br /><FONT FACE="Courier">192.168.1.1</FONT>>];
Phone1 [label=<Phone 1<br /><FONT FACE="Courier">192.168.1.102</FONT>>];
Phone2 [label=<Phone 2<br /><FONT FACE="Courier">192.168.1.103</FONT>>];
Laptop [label=<Laptop<br /><FONT FACE="Courier">192.168.1.104</FONT>>];
SmartTV [label=<Smart TV<br /><FONT FACE="Courier">192.168.1.105</FONT>>];
isp->router->{Phone1, Phone2, Laptop, SmartTV};
isp->neighbor->neighbor_wifi;
{rank=same;isp,neighbor};
}](_images/graphviz-08bfa300eae6678da15c2f223b84bb93e5a58788.png)
Your home network with example IP addresses#
Your router is a little computer in itself and it has settings where you can change your
Wi-Fi password, set up a guest network, adjust security settings, and other things. It
doesn’t have a screen or keyboard like your laptop so it presents its user interface
through a web browser. To get to it, simply point your web browser to its IP address,
which is very often 192.168.1.1 or 192.168.0.1. If you struggle, check the bottom
of your router for a sticker that says what its default address is.
Setting a strong Wi-Fi password#
With more smart-this and smart-that in the home, the security of your Wi-Fi router is fairly important. It’s easy for people driving around with laptops to get onto unsecured networks or ones with easy-to-crack passwords (they’re called war-drivers). It’s no problem to tote around terabytes of pre-hashed passwords (called rainbow tables) and try to get in. So try to come up with a password that is unlikely ever to have been used before. As always, no single dictionary words.
Note
Did you know? Wi-Fi doesn’t really stand for anything. It’s just riding upon the good reputation of Hi-Fi stereo equipment, which means High Fidelity. “Wireless fidelity” would make no sense at all.
You can use your password manager to make a random Wi-Fi password. This might annoy your family if it’s too hard, but you can at least make it easy to get on by generating a 2-D barcode (QR code) in a special format. Websites like qifi.org do this for you in a few seconds. Once it’s done, anyone can use a barcode scanner app and just scan it to get online. Just don’t make it visible from any windows! Also beware that some devices like printers will still require you to type the password in manually.
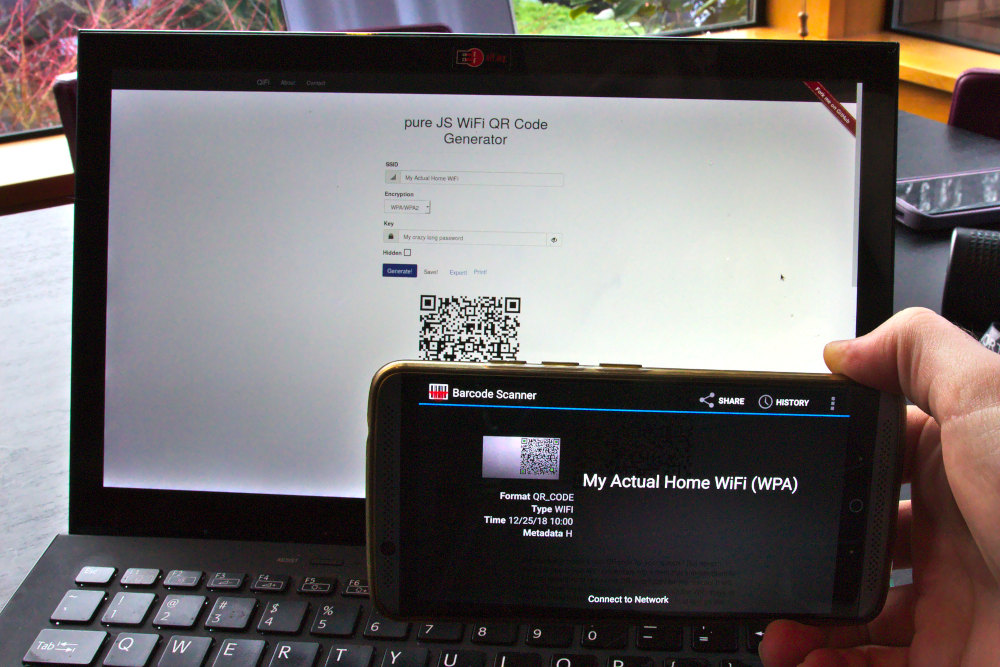
Scanning a QR code to connect to Wi-Fi.#
Guest networks#
Many Wi-Fi routers allow you to set up a separate network for guests. Doing so gives them unfettered internet access without exposing your devices to any viruses or misbehavior they may be dealing with.
It may be wise to connect your Smart TVs and other devices with ulterior motives to the guest network. Some devices have been known to monitor other devices on the network to try to figure out how to send better ads or otherwise track you. If they’re on a different network they can’t watch your phone and laptop.
Avoiding DNS hijack#
Have you ever mistyped a web address only to be greeted by a page with ads from your
internet service provider (e.g. Comcast)? That’s something they can do because they are
providing the internet phone book of lookup tables between web page names and actual
server IP addresses (more on this phonebook system, called DNS, in
Publishing). They may also be slower and less secure than some of the other
options. You can adjust your DNS settings in your router’s setup (near where you set the
Wi-Fi password). You’re looking for DNS Server settings or Custom DNS. I recommend
using CloudFlare’s DNS entries for good security and performance:
Primary (IPv4) |
|
Secondary (IPv4) |
|
Primary (IPv6) |
|
Primary (IPv6) |
|
They have detailed instructions at https://1.1.1.1 if you’re interested.
Opening ports#
Your router acts as a firewall between the dangerous public internet and your devices in your home. Sometimes you may need to carefully poke holes in this firewall for one reason or another (you want to access your security system from afar, or your video game needs to communicate with peers for multiplayer, or something else). This is done in your router configuration, near the Wi-Fi password setup. Search for Firewall settings and/or Port Forwarding. Once you find it, you’ll see a table similar to this:
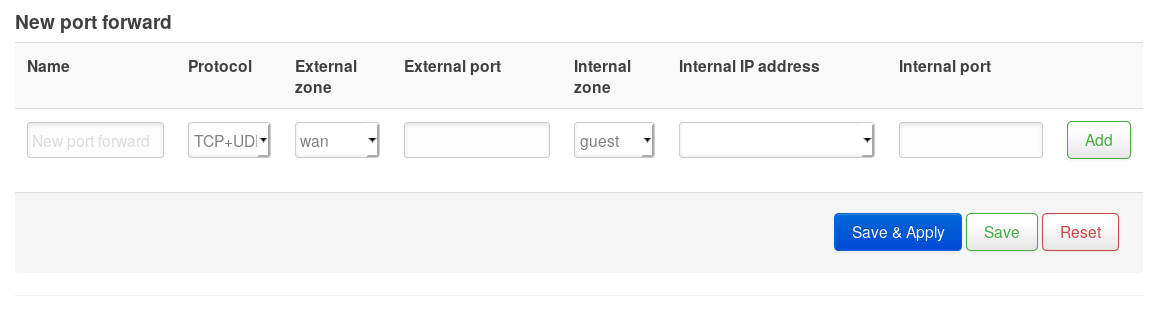
In this form you choose which port number to forward and which internal device it should
get forwarded to. So if you had a Raspberry Pi at 192.168.1.106 you wanted to remote
into on Port 22, you’d enter 22 for both the internal and external port, and the IP
address for internal IP address. Make sure that Raspberry Pi is on lock-down though because
it will be subject to Script Kiddies trying to hack into it almost immediately. Consider
using a non-standard port number as the external port to reduce this.
Virtual machines#
Virtual Machines (VMs) are programs that emulate a fresh, empty computer. They allow you to run an entire other operating system as a program on your computer. At home, this can be really useful if you have a particularly curious family member who really wants to mess around with computers, but you don’t want them to break yours. You can let them mess around all they want in the virtual computer on your computer!
Professionally, they’re great for seeing how your products or services work on other kinds of computers. If you’re making a website on a Mac and want to make sure it works in Windows, a VM can help [2].
They can also be useful for trying out a program or operating system that you don’t feel comfortable with or trust for some reason. If it does have a problem, you can just reset the VM to its initial state. This is a phenomenal way to try out things like Linux that you’re just curious about getting a feel for. It’s also how security researchers research and monitor known computer viruses.
A few Virtual Machine managers exist, but let’s just get started with one called VirtualBox.
OS |
Installation method |
|---|---|
Windows |
|
Linux |
|
macOS |
|
When you run virtualbox it will pop up a window from which you can either import
pre-made virtual machine “appliances” or make new ones. Here are the steps to try out
Ubuntu Linux in a VM:
Download the latest Ubuntu image from here.
Open
virtualboxand chooseMachine → New. Name itUbuntuand set type toLinux, version:Ubuntu_64.Click through the defaults for Memory size, hard disk, etc. (or adjust as you please)
Click
Startto boot the empty machine.It will prompt you for a start-up disk. Click the browse button and choose the downloaded Ubuntu
isoimage.Click Start and the Ubuntu installation process will begin!
If you haven’t been exposed to Linux before, bask in the glory of how nice it is.
Note
Related to VMs, you’ll also hear about containers which set up isolated “jails” for programs to run in while sharing the same host operating system. Containers require less hard-disk space, are faster to spin up and down, and require fewer system resources, so they’re really popular in modern cloud-based data centers and infrastructure. The Docker container manager is the most popular. Some software developers/vendors are distributing their programs these days in docker containers to simplify the setup process for users.
Nostalgia alert#
It’s sometimes fun to re-live your younger years by setting up virtual machines with old versions of software like DOS and Windows 3.1 (or whatever was around when you were a kid). You can get the images of the installation discs at places like WinWorld and then mount those images one by one as floppy disks in VirtualBox and have a good old time [1]. Designasaurus, anyone?
Along these lines, the DOSBox project is a better way to
actually play old games on your current computer. It will integrate nicely with modern
video and audio hardware, which is harder to do with pure virtual machines. It’s in your
package managers (dosbox).
MS Works running on DOS 6.22 on a Virtualbox VM.#
Ad-blockers#
Ads are like a sad knock-off of Santa Claus. They track us and watch over our shoulders as we shop. They try to get us to buy boots for months after we buy some boots. We can’t afford to give up precious brain cycles. If they ever sneak onto Netflix, it’s game over. You can do a few things to reduce your shopper footprint in the nefarious systems of commercial retail if you so desire. Here are some options:
Use the Firefox web browser instead of Chrome or Edge, and install the EFF’s Privacy Badger plugin and/or the uBlock ad blocker. Google at its core makes most of its money off of advertising. Firefox works on your phone as well as on your laptop. Try using your package manager to install
firefoxif you don’t have it yet.Enable the “DO NOT TRACK” setting in your web browser.
If you’re into Raspberry Pis (small $30 computers) get another one and install Pi-Hole on it. This is slightly advanced (you have to adjust your Wi-Fi router settings as part of the setup) but is really effective in the home. It “hijacks” the internet phonebook system (DNS) that maps human-readable internet names (such as
https://this.com) to the actual IP addresses that underlie networking (like10.0.0.1) and compares them to a crowd-sourced blacklist of advertisers and baddies. If the name is on the blacklist, the request just gets sent to the abyss. Ads on all your devices on your home network simply disappear. It’s pretty nice. My Roku tries to talk to a blacklisted site like 5,000 times per day but can’t get through. Muahahaha.Turn off your Wi-Fi and Bluetooth when you’re in malls. They’re apparently watching metadata from your phone’s modem as you walk around even if you don’t connect to the hotspot. Look up “people counters” if you don’t believe me.
Just don’t ever shop or carry a cell phone.
Move to Antarctica.
Using a VPN Service#
Virtual Private Network (VPN) providers are useful for peace of mind, especially while traveling or in places where you don’t trust the Wi-Fi operators (hotels, coffee shops, on travel with sensitive business information, hacker-friends’ houses, etc.). When you get on a network, anyone else on the same access point and especially the people operating it can “sniff” the network to see what websites you’re going to and, if there’s no green lock in your browser window, what information you are sending and receiving (though more and more websites have the green lock these days as a best practice).
You can pay a VPN provider that will help with this. You can click a button on your computer and it will create a strongly-encrypted connection between you and the VPN server. Then you will tell the VPN server which sites you want to interact with and it will go out and do your bidding, sending the results back to you through the super-encrypted channel. Anyone between you and the VPN is now in the dark as to what you’re doing online. They can’t see what servers you interact with nor what data is being sent to and fro. Instead of trusting dozens of operators and their staff along the way, you only have to trust the VPN provider. Huzzah!
![digraph fig {
#graph[margin=0.2, nodesep=0.3, ranksep=0.4];
node [shape=record];
laptop [label="Your laptop"];
guests [label="Other guests"];
hotel [label="Hotel Wi-Fi"];
local_operator [label="Local Wi-Fi contractor"];
laptop -> guests -> hotel -> local_operator [dir="both",color="red",style="dashed"];
local_government [label="Local government"];
routers [label="Nefarious routers"];
website [label="Website"];
local_government->routers->website [dir="both", color="red",style="dashed"];
{rank=same;laptop, local_government}
{rank=same;guests, routers}
{rank=same;hotel, website}
local_operator -> local_government [dir="both",color="red",style="dashed"];
}](_images/graphviz-baee10cb6f5be64687beb16cc37b339161198715.png)
Browsing the web from a hotel. Everyone along the way can see any non-TLS (i.e. green lock in browser window) traffic and all metadata, including what sites you’re browsing and for how long. This is bad if you don’t want people along the way to know what you’re doing.#
![digraph fig {
#graph[margin=0.2, nodesep=0.3, ranksep=0.4];
node [shape=record];
laptop [label="Your laptop"];
guests [label="Other guests"];
hotel [label="Hotel Wi-Fi"];
local_operator [label="Local Wi-Fi contractor"];
laptop -> guests -> hotel -> local_operator [dir="both",color="green"];
local_government [label="Local government"];
routers [label="Nefarious routers"];
VPN [label="VPN operator"];
website [label="Website"];
routers2 [label="Oblivious routers"];
local_government->routers->VPN [dir="both", color="green"];
VPN -> routers2 -> website [dir="both", color="red",style="dashed"];
{rank=same;laptop, local_government}
{rank=same;guests, routers}
{rank=same;hotel, VPN}
local_operator -> local_government [dir="both",color="green"];
}](_images/graphviz-d84a0951c4e37ae49c308579e72fb1cef737fe56.png)
Browsing the web through a VPN hides what you’re up to from almost everyone. After the VPN service, metadata is available but it’s anonymized to everyone except the VPN operator themselves. So you only have to trust the VPN operator in this scenario.#
The downside here is that your connection will be at least a little slower since it has to route everything through the VPN service, wherever it may be.
Companies offering VPN services include ExpressVPN, Private Internet Access VPN, IPVanish, NordVPN, Cyber Ghost, and many others. Prices are borderline $40–$50/year.
Instead of connecting each of your individual devices to the VPN, you can alternatively choose to configure your Wi-Fi router as a VPN client (only certain router models have this feature). I’m not sure this makes too much sense at home unless you really don’t trust your ISP. Some people actually take a travel router with them on trips that automatically connects to their VPN, and they only connect through it. That is particularly neat.
Depending on your interests, you can also run your own VPN service right from your home as discussed in Set up your own VPN Server.
The Onion Router and the dark web#
Speaking of network security, we have to mention the ultimate system in this regard: The Onion Router (Tor) and the so-called dark web. The underlying technology was started by the US Naval Research Laboratory and later well funded by DARPA. Its job is to get you as close as possible to truly anonymous internet communication where the user doesn’t have to trust anyone along the communication pathway. It prevents people from monitoring what you browse and it prevents the sites you visit from knowing where you are.
Web server admins can put their web page up as an onion service and it’s supposed to be hard to figure out who’s operating it and hard to shut down.
It’s used by secret agents, hacktivists, normal people who want to try it out, people who want to look something sketchy up without leaving a trace, and many other legitimate people.
It’s also used by criminals. There is a thriving black market for drug sales coordinated through Tor and other illicit stuff.
It’s called the onion router because it has many layers. The Tor network
consists of a bunch of nodes run by volunteers. These nodes pass encrypted onion traffic
from node to node. When a user sends a request to browse to website x, their system
chooses a random pathway based on a network directory server, puts a bunch of layers of
encryption over the request, and tosses it into the network. The first Tor server decrypts
the first layer and finds the address of another Tor server so it passes the binary blob
along. The second server pulls off the second layer, and so on. Eventually, when
no layers remain, the website to visit is revealed. Whichever random server in the Tor
network gets this goes out, grabs the requested information from the website, and sends
the request back through the Tor network to the original user in an equally randomized way.
Tor is not impossible to see through. Governments monitoring networks can know when you’re
on Tor and if they really want, they can have their hackers use one of the thousands of
unpublished major computer bugs (called zero-days) to just get on your computer and
watch what you’re doing directly. Or they can use end-to-end correlation to guess what
you’re doing. If you send a request that causes website x to send you some exact
number of bytes, those bytes will eventually go to your computer. By monitoring the entire
internet, governments can say, “OK well these 3987345 bytes came out of that server and,
ope! 3987345 encrypted bytes just went into this guy’s computer way over here right after
that! I think I know what they’re doing!”
Tor can be useful. But don’t think you can get away with something horrible.
Using Tor is actually really easy. The Tor Project folks have set it up so you just download their web browser and it auto-connects to Tor and you’re off. You can find phone apps that trivially connect to it as well.
From your package manager:
OS |
Installation method |
|---|---|
Windows |
|
Linux |
|
macOS |
|
Android |
Download |
Launch Tor Browser (it’s in your Start Menu in Windows) and you’re good to go. Don’t go logging into your Facebook now though, that would deanonymize you rather quickly. On second thought Facebook did make a Tor Service address (https://facebookcorewwwi.onion/) and that might be a fun first Tor Service to try to access. This would be useful to access your Facebook when you’re not supposed to. Again, if Facebook is banned where you are, connecting to Tor might raise some red flags too so just be careful.
Note
Due to the nature of Tor, browsing the web through it is inherently slower.
Planning a night of star-gazing#
To wrap up this chapter, let’s leave the network and take a step out into the yard or a nearby park. Have you ever wondered which star, planet, constellation, or moon you’re looking at in the night sky? Ever need to know exactly when an eclipse is going to peak at a particular location? If so, you’re in luck because your computer and phone can easily have all this information on it. Stellarium is an open-source planetarium for your computer, available on all platforms, and Androids and iPhones have apps with some related features.
OS |
Installation method |
|---|---|
Windows |
|
Linux |
|
macOS |
|
Android |
Download |
iPhone |
Download |
Stellarium allows you to choose your location and date/time (defaults to your here and now) and shows you the sky. You can search for particular planets or constellations, figure out which side of the house to set up for an upcoming eclipse, even zoom way in on deep-space objects like the Horsehead Nebula. You can step through in real-time or in fast-forward to see how the stars and planets will shift over the night or across the seasons. If you have a motorized telescope, Stellarium can hook into it and steer it to (and track) any visible object. It’s a whole lot of fun and you or your family members will have a wonderful time searching around on it. It’s basically a sky simulator.
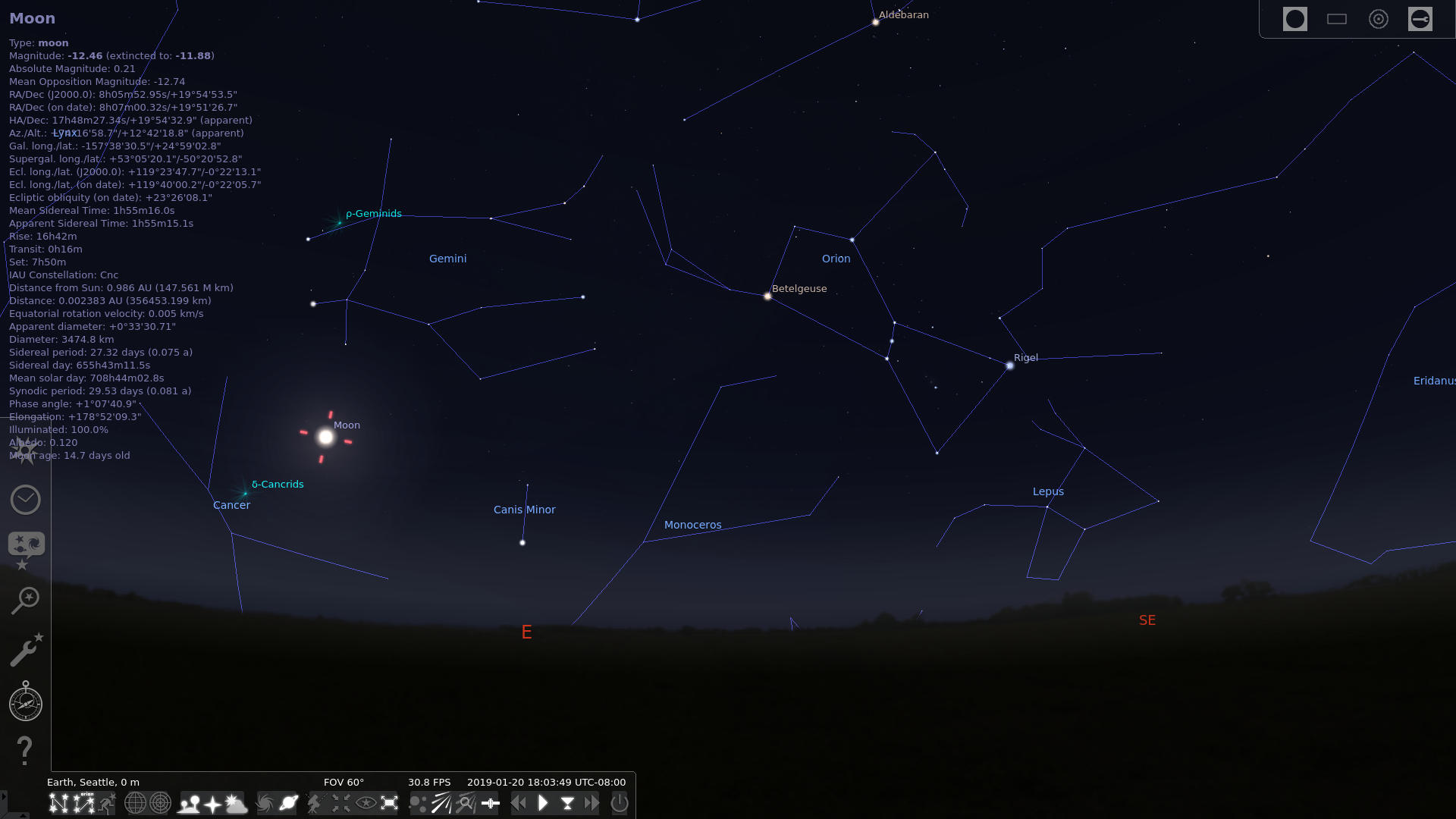
Stellarium showing the night of a lunar eclipse.#
After you have Stellarium installed, open it and you’ll see its best estimate of your current sky in your current location. If you push the mouse to the left edge, some widgets will appear. The first one lets you adjust your location, and the second lets you adjust the time. Change these to see how the sky changes. If it’s not night, try spinning the clock until it is night. When you push the mouse to the bottom of the screen, you’ll see various toggles to turn on and off constellation labels and other points of interest. Now just click and drag in the screen to turn your view, and scroll with the mouse wheel to zoom in and out. If you click an object like the Moon, you’ll see all sorts of interesting information about it. This is a wonderful program for people of all ages.
That’s all we’ll cover for the home. I hope you are already enjoying some of your newfound superpowers!
Footnotes